
PVA series – authentication in Power Virtual Agent
Table of contents:
Today Microsoft already released some of the features, which were planned to be released on 2nd of December 2019, in their “new” product: Power Virtual Agent. One of them is “Authentication”. In this post I will help you to set up Azure Active Directory as an oAuth2.0 authentication endpoint.
How does authentication in PVA works?
Once you put authentication action in the conversation flow and conversation reaches that point:
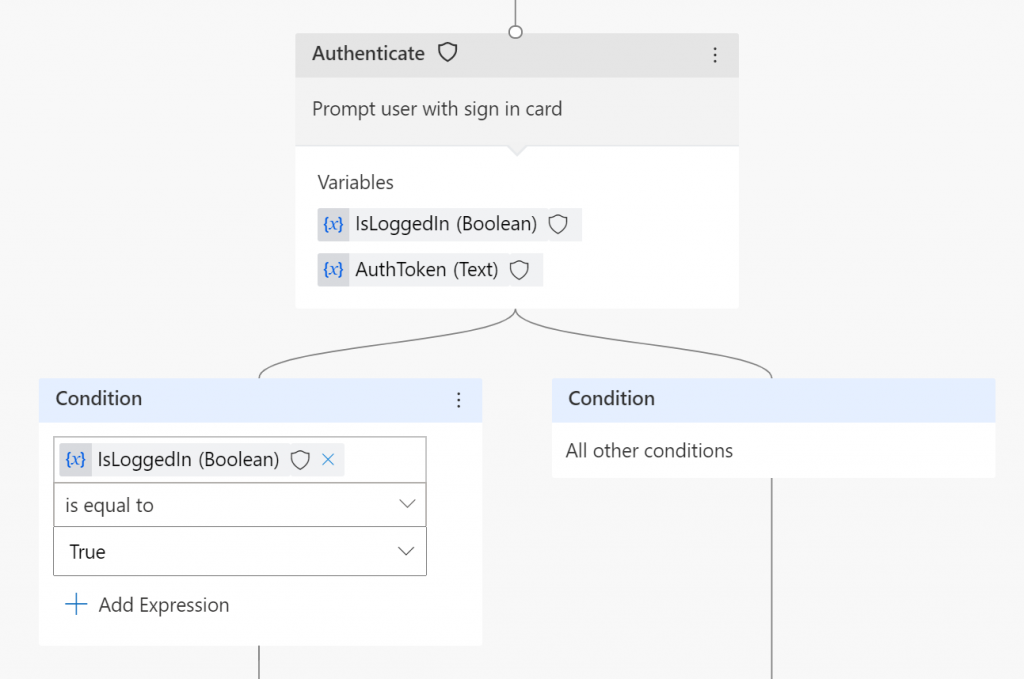
It will display a card with a button to the user, that once clicked will generate an OTP that user has simply to copy and paste into a chat window:
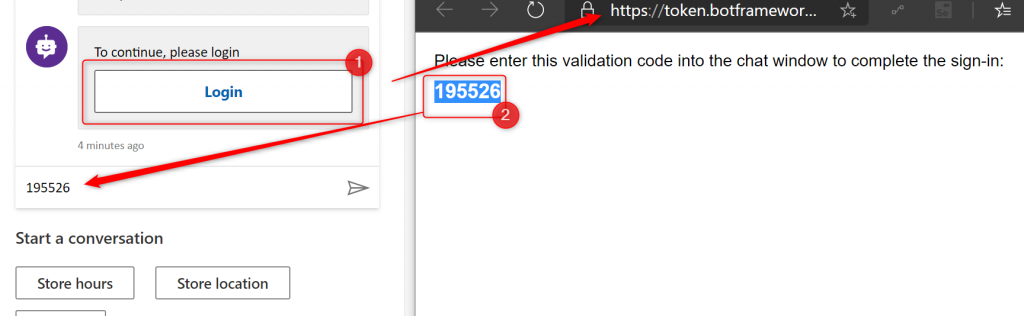
Once user successfully logs in, the there are two variables that are being used in flow after that:
- IsLoggedIn – boolean variable, true if logged in (what a surprise :P)
- AuthToken – this is simply a bearer token generated for the user
Configuration
To access authentication settings of your bot you have to navigate to the following URL: https://powerva.microsoft.com/#/manage/authentication.
Important! You can define a single authentication endpoint per each bot.
The page is showing an empty form, actually not very easy to fill with information, if you are not an expert in Azure AD 🙂
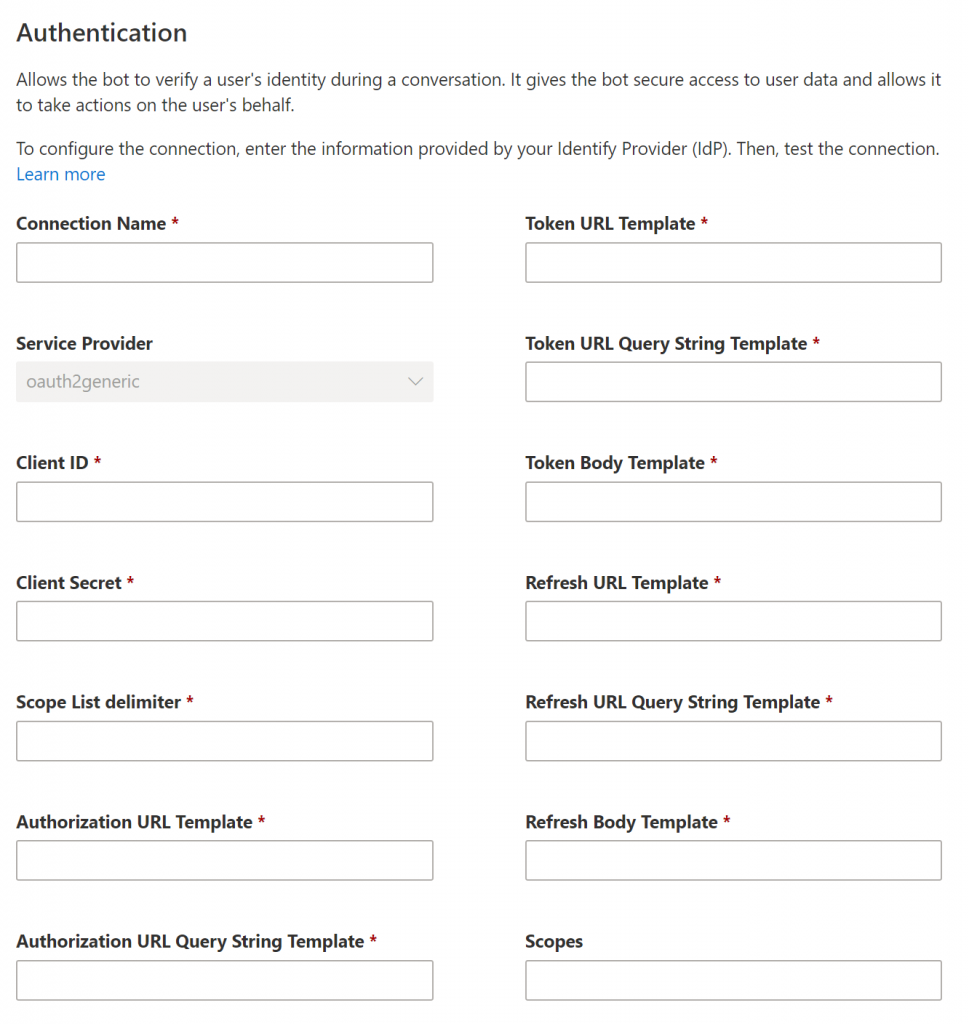
Luckily, there is the documentation written quite well, that helps us to set values for these fields if we want to use AAD as the provider: https://docs.microsoft.com/en-us/power-virtual-agents/configuration-end-user-authentication
| Field name | Value |
|---|---|
| Connection name | Connection name |
| Service Provider | Power Virtual Agents only supports generic OAuth2 providers. |
| Client ID | Client ID of the Azure app (read further) |
| Client Secret | Client Secret of the Azure app (read further) |
| Scope List delimiter | Use: , |
| Authorization URL Template | https://login.microsoftonline.com/common/ oauth2/v2.0/authorize |
| Authorization URL Query String Template | ?client_id={ClientId}&response_type=code&redirect_uri={RedirectUrl}&scope={Scopes}&state={State} |
| Token URL Template | https://login.microsoftonline.com/common/oauth2/v2.0/token |
| Token URL Query String Template | Use: ? |
| Token Body Template | code={Code}&grant_type=authorization_code&redirect_uri={RedirectUrl}&client_id={ClientId}&client_secret={ClientSecret} |
| Refresh URL Template | https://login.microsoftonline.com/common/oauth2/v2.0/token |
| Refresh URL Query String Template | Use: ? |
| Refresh Body Template | refresh_token={RefreshToken}&redirect_uri={RedirectUrl}&grant_type=refresh_token&client_id={ClientId}&client_secret={ClientSecret} |
| Scopes | For the purpose of authentication it should be: openid |
Azure app
Since the configuration requires the app’s client id and secret key, also the scope name, you have to configure that app in AAD.
To do that open https://portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/RegisteredApps – app registrations blade under Azure AD blade. Next create “new registration”:
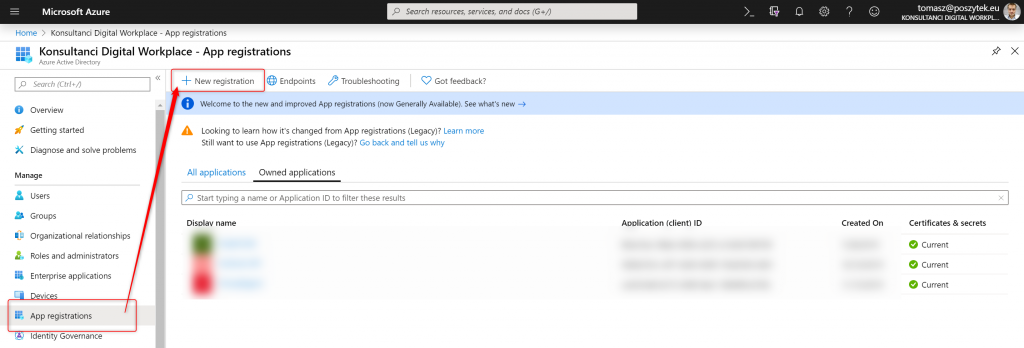
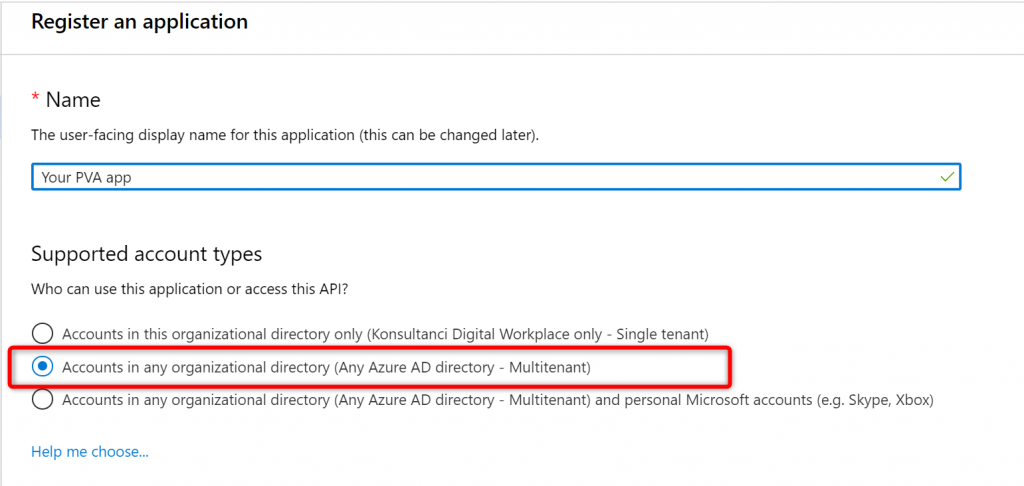
Next define its name and choose “Multitenant” option for the supported account types:
Once the app is registered, you must configure redirect URL. To do that do the following:
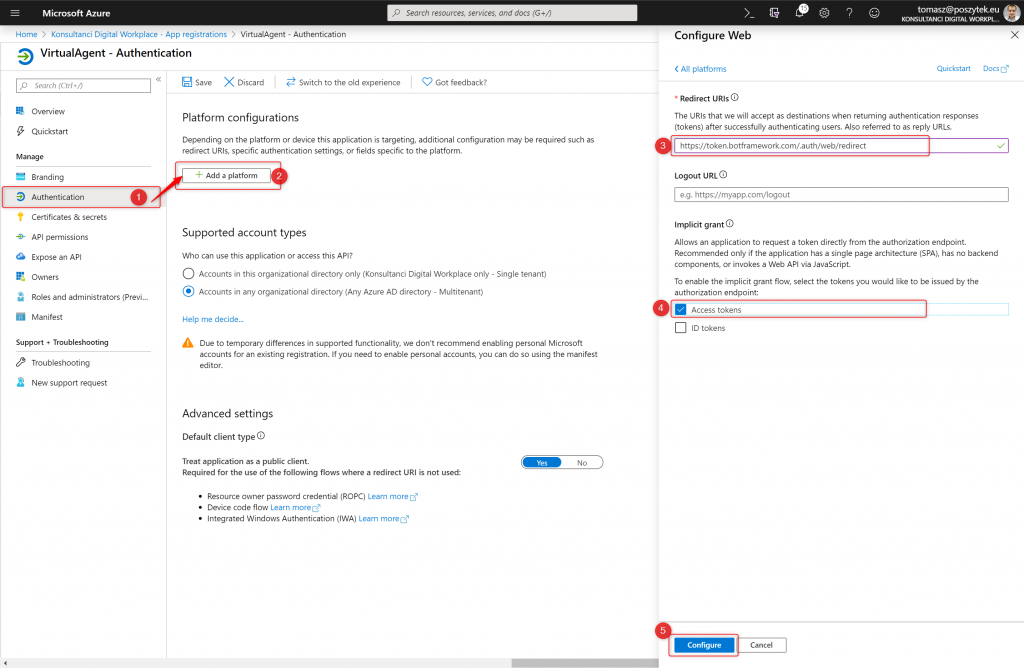
- Next go to the “Authentication” blade
- Click “Add a platform” button
- Type: “https://token.botframework.com/.auth/web/redirect”
- Select “Access tokens” option
- Hit “Configure”.
Next you have to also grant permissions for the app. To do that do the following:
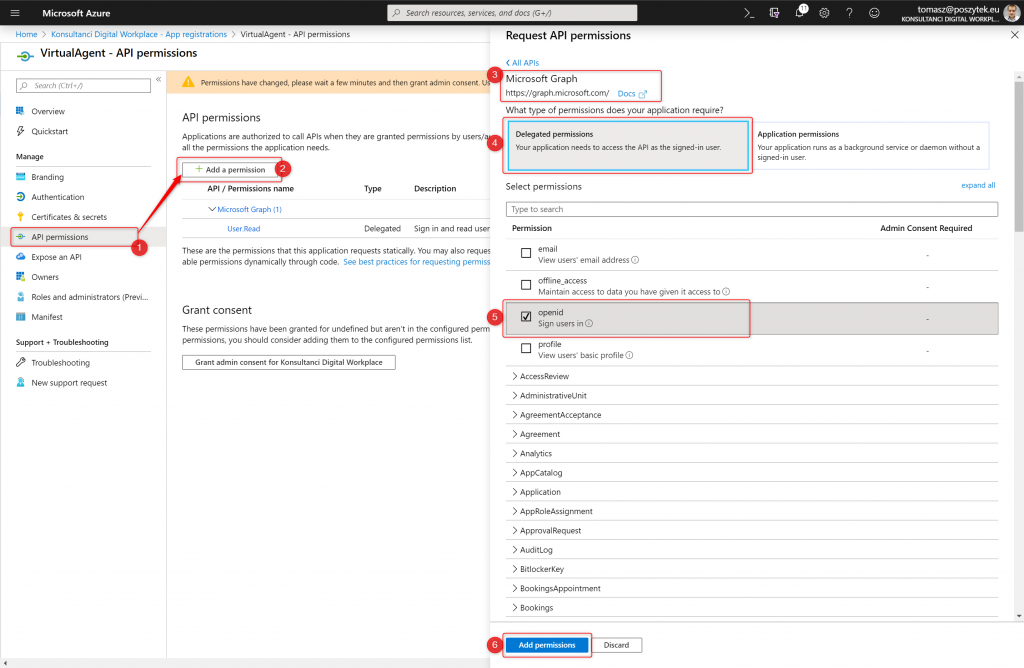
- Go to “API permissions” blade
- Click “Add a permission” button
- Choose “Microsoft Graph”
- Hit “Delegated permissions”
- Select “openid” option
- Hit “Add permissions” button
Finally go to the “Certificates & secrets” and generate new secret key:
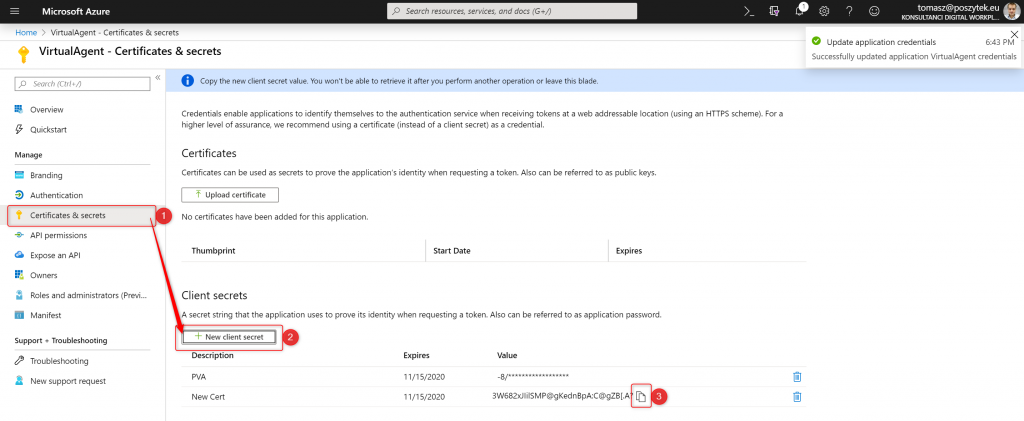
Then copy its value and paste it in the Power Virtual Agent configuration window. Finally go to the “Overview” blade to copy “Client ID” value:
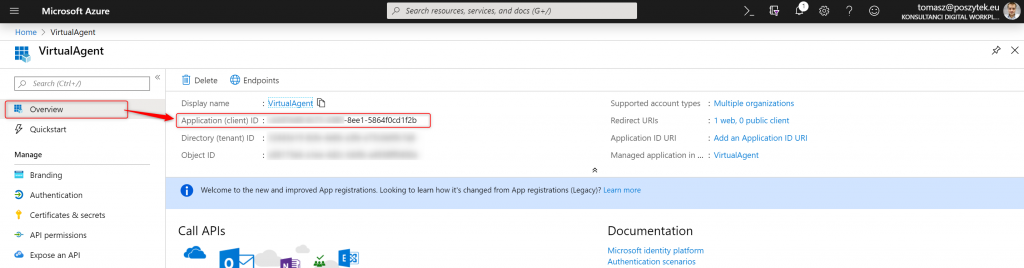
That’s it! Azure App is registered and configured. Copy it’s key and id, and paste in the Power Virtual Agent configuration screen.
I hope this post will help to save hours of searching and figuring out how to configure the authentication with AAD for PVA. Leave me a comment if you need any support!


Shaun Leise
This saved me hours, thank you!
One thing I noticed:
If you copy and paste the values from your table above for Authorization URL Template, Token URL Template and Refresh URL Template there is an erroneous space ” ” before the word oauth2 which needs to be removed for the URL’s to work correctly.
Tomasz Poszytek
That is correct. I added there a new line to improve the layout. But sure, those white spaces should be removed.
Pingback: Dynamics 365 Project Service Automation: Creating a Project with Power Virtual Agents
joe Pirelli
For MS AD (and possibly others) you will need to use the app custom endpoints instead of the ambiguously named ones.
Something like this:
https://login.microsoftonline.com/{appid guid}/oauth2/v2.0/authorize
https://login.microsoftonline.com/{appid guid}/oauth2/v2.0/token
Tomasz Poszytek
Actually the described configuration works just fine. Appid (clientid) is passed as a parameter.
Chamika
this token cannot be used as access token for a custom api. to use that response_type should change to id_token+token. but once i change it gives me bad request while valid token is there in the redirect url
Tomasz Poszytek
I haven’t checked with custom API tbh. Did you try to reach out to Microsoft explaining your case?
Bhaskar
Added authentication feature and added bot to teams (Working fine on Web page and while testing it on PVA site)
But login button doesn’t do anything in teams chat
Am i missing something?
Tomasz Poszytek
Once clicked it should automatically authenticate you. Not like when embedded on the page, when you need to copy and paste the confirmation code.
Bhaskar
Yes, ideally it should log the user in automatically but nothing happens when I click on Login button
https://imgur.com/0ffM7k4
Tomasz Poszytek
Does it work when you embedd the agent on regular page? Not in Teams?
Bhaskar
It is working in Microsoft sample website
https://imgur.com/1hCPnTa
Tomasz Poszytek
I have no idea then. Use option inside Power Platform admin center to raise a support ticket. That should definitely work.
Rooshan
Hi Tomasz,
Were you able to figure out Bhaskar’s issue? i have the same issue. the login button is not doing anything when i am using it inside MS teams for web, desktop and android versions. it is only working in iOS. I have no clue about the possible problem
Tomasz Poszytek
Nope. No new information. I recommend contacting Microsoft Support for this one.
Tomasz Poszytek
I believe you saw this post of mine: https://poszytek.eu/en/microsoft-en/office-365-en/pva-en/pva-series-add-power-virtual-agent-to-teams/ – I tried it and this is working fine.
Dhiraj Agarwal
Very nice and clean article. We could able to follow and get our authentication stablished.
Tomasz Poszytek
Thanks! I’m glad it helped you.
Andrew
hi Tomasz
would you please show example of how to use the generated AuthToken for retrieving user name / email ?
many thanks
Andrew
Tomasz Poszytek
Sure, please follow details described in this post: https://poszytek.eu/en/microsoft-en/office-365-en/pva-en/pva-series-user-context-in-power-virtual-agent/
Pingback: Day 12 – Configure Azure AD Authentication in PVA – Power Community
Kevin
Is there a way to pass the user variables to another a topic once user has been authenticated?
Tomasz Poszytek
Hi! Not yet. Global variables are coming. Once they arrive, you will be able to use them to pass data from one topic, to another. Also – SSO is coming. So possibly this will solve your issue 🙂
Source: https://docs.microsoft.com/en-us/power-platform-release-plan/2020wave1/power-virtual-agents/planned-features
Tricia Sinclair
Thank You Tomasz!! This really helped me alot!
Tomasz Poszytek
Hi Tricia 🙂 I am more than happy to help you! Keep safe.
Pingback: PVA series – authentication in Power Virtual Agent – Tomasz Poszytek, Business Applications MVP – More Stuff 2 Read [Quite Sparsely]
Leo Perez
Is there a way to trigger a topic if the authentication failed? I was able to configure my bot to use Single Sing-on, but my problem is when a user is anonymous. I want to display a generic message to the user if he/she was not authenticated instead of displaying the log in card. Can you help me with this one.
I already tried the same code as the bot to initiate conversation / greetings, but I have no luck with it. I don’t know what webchat or direct line event should I use.
Tomasz Poszytek
I haven’t been configuring SSO myself, but maybe there’s a way to access authenticated user’s variables and if empty – navigate to another topic?
Vikash Pathak
Login button doesn’t work in iPhone.
can you please let me know if there is nay workaround?
Tomasz Poszytek
Haven’t really tried using this on iphone. Try asking your question on the forum: https://powerusers.microsoft.com/t5/Power-Virtual-Agents-Community/ct-p/PVACommunity
Ernesto
How to configure single sign-on with Azure Active Directory in Power Virtual Agents
:C
Tomasz Poszytek
Would that help? https://docs.microsoft.com/en-us/power-virtual-agents/configure-sso
Duncan
Hi Tomasz. Do you know if this approach still works today (Jan 2024)? We tried it and can only get users outside our tenant to authenticate if we add them as a guest to our tenant. If they aren’t added to our tenant as a guest, the user gets an error message that the user is not in the same tenant as the authentication app and so cannot log in.
Tomasz Poszytek
I don’t really know. But as I look at the documentation, it looks quite similar 🙂
https://learn.microsoft.com/en-us/microsoft-copilot-studio/advanced-end-user-authentication?tabs=web